Cyber threat intelligence (CTI) has become indispensable for security teams looking to get ahead of the onslaught of threats targeting organizations. By leveraging insights into the tactics, techniques, and procedures of bad actors, you can shift your security program from reactive to predictive.
In this comprehensive 2,500+ word guide, we‘ll provide an in-depth look at what CTI entails, why it‘s critical for your organization in today‘s threat landscape, the diverse sources and types of threat intelligence, the growing impact of AI and machine learning, actionable benefits for your security team, pitfalls to sidestep, and an overview of leading CTI vendors.
What is Cyber Threat Intelligence and Why Does it Matter?
Cyber threat intelligence refers to carefully analyzed information about existing or emerging menaces that may impact your organization. It provides vital context around threats to inform faster, smarter security decisions.
As Gartner defines it, "CTI consists of evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice about an existing or emerging menace or hazard to your assets. CTI can inform decisions regarding your organization‘s response to those threats."
The key goals of threat intelligence are to:
- Understand the motivations, behaviors, and capabilities of threat actors targeting you
- Detect security incidents and compromised assets faster
- Reduce risk by continuously improving your security strategies and controls based on intelligence
You can derive threat intelligence from these key sources:
-
Open Source Intelligence (OSINT) – Publicly available information from sources like social media, technical blogs, news sites, and code repositories. A prime example is leveraging Twitter to detect emerging phishing campaigns or using Reddit to observe hacker forum chatter about new attack techniques.
-
Human Intelligence (HUMINT) – Information gathered directly from human sources. For instance, interrogating an apprehended cyber criminal about their methods, sponsors, and plans or soliciting tips from security researchers and insiders involved in underground communities.
-
Signals Intelligence (SIGINT) – Intelligence derived from analyzing intercepted communications networks and electronic signals. An example is identifying a command and control server based on unusual traffic patterns to detect botnet activity.
-
Technical Intelligence (TECHINT) – Insights gained from analyzing an adversary‘s tools, capabilities, vulnerabilities, and infrastructure. Reverse engineering a new strain of malware can reveal attacker behaviors and code reuse.
The need for comprehensive, continuous threat intelligence has never been greater. Here‘s why it‘s so critical for security leaders today:
- Accelerating Digital Transformation – As more business functions and data shift online and to the cloud, your organization‘s attack surface and risks are multiplying exponentially. Threat actors now have more targets and vulnerabilities to exploit.
- Threat Actor Innovation – From nation states to cyber criminals, bad actors are using increasingly sophisticated techniques like supply chain compromise and deepfakes to evade defenses. Between 2020 to 2021 alone, ransomware attacks grew by 105% according to SonicWall threat data.
- High Cost of Breaches – IBM estimates the average cost of a data breach now exceeds $4 million. For organizations in healthcare or finance, it can be dramatically higher. Breaches can also do massive damage to customer trust and reputation.
- Increasing Regulatory Obligations – Compliance mandates around cybersecurity and data protection continue to proliferate worldwide, with steep penalties for violations. Threat intelligence strengthens compliance audits.
Threat intelligence enables your security team to focus on defending against the most pertinent risks to your organization and industry. With CTI, you can work proactively instead of reactively.
Key Sources of External and Internal Threat Intelligence
Effective cyber threat intelligence relies on a combination of both external and internal intelligence sources to build a comprehensive picture tailored to your unique risk profile.
External Threat Intelligence Feeds
-
Open Source Intelligence (OSINT) offers a treasure trove of publicly available threat data. This includes discussion forums, code repositories, paste sites, technical blogs, social media platforms, dark web sites, and more. Specialized search tools like Recorded Future‘s Temper AI can mine this data at scale using natural language processing and machine learning. [Analyst firm MarketsandMarkets predicts the OSINT market will grow 17% CAGR to reach $30 billion by 2025.]
-
Commercial Threat Feeds provided by specialized cyber intelligence firms and vendors track and analyze tens of billions of security events and data points using big data pipelines and artificial intelligence algorithms. These curated feeds typically include enriched threat indicators like newly observed malicious IP addresses, phishing URLs, malware SHAs, or compromised credentials associated with known bad actors. Popular options include Recorded Future‘s Intelligence Cards, Anomali Match, Flashpoint, and more.
-
Industry Sharing Initiatives enable anonymous sharing of threat data between participants across sectors like finance, energy, telecom, and retail. This allows members to benefit from collective intelligence to boost defenses. Examples include the Financial Services Information Sharing and Analysis Center (FS-ISAC), National Health ISAC (NH-ISAC) and Cyber Threat Alliance (CTA).
-
Government Sources like CERTs and law enforcement agencies provide timely advisories about heightened threats, recent widespread attack campaigns, or activity by adversaries in a specific region.
Internal Threat Intelligence
-
Security Telemetry gathered from your firewalls, endpoint detection, intrusion prevention systems, and other security tools provides visibility into the specific reconnaissance activity and attacks targeting your users and infrastructure. Identifying these patterns helps focus threat hunting.
-
Log Aggregation and SIEM solutions should correlate internal and external threat signals to detect security incidents early and speed high-fidelity alerts for urgent response. Machine learning models can baseline "normal" activity to detect anomalies.
-
Sandboxing and Malware Analysis allows you to safely detonate potential malware samples and analyze behavior to gain insights about an attacker‘s playbook which can inform detection rules.
-
Incident Response Data accumulated from past investigations and remediation of threats offers tactically relevant "lessons learned" that can strengthen ongoing defenses against that threat actor or their techniques.
-
Vulnerability Assessments shine a light on your organization‘s weaknesses and gaps that adversaries could exploit. This enables you to smartly prioritize patching and hardening efforts based on risk.
The most effective approach combines continuous monitoring of both external intelligence and internal security telemetry to provide comprehensive visibility attuned to your organization‘s specific threat landscape and priorities.
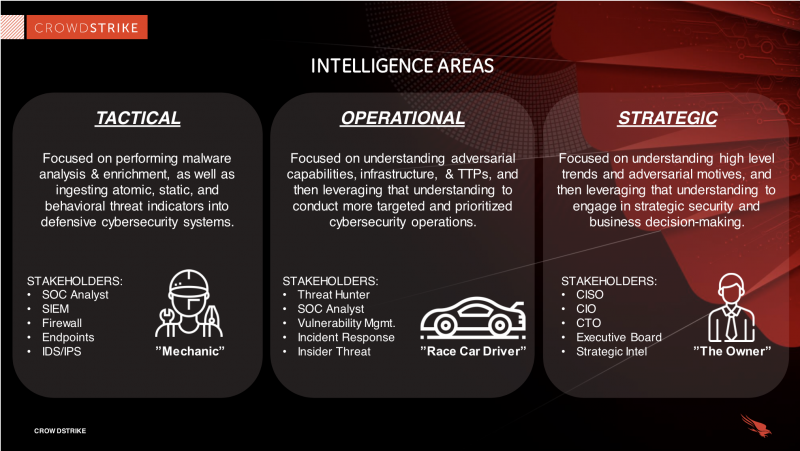
Types of Cyber Threat Intelligence
There are three primary types of cyber threat intelligence, each serving different functions and audiences within your organization:
Tactical Threat Intelligence
Tactical CTI focuses on indicators of compromise and other technical artifacts that allow you to quickly detect and block known threats like malware, malicious IPs, phishing sites, and more. It directly helps improve your defenses and speeds up incident response.
Key Consumers: SOC analysts, incident responders, network defenders use tactical IOCs to search for signs of compromise across the environment. An example would be threat feeds of newly observed phishing sites that get ingested into a secure web gateway to block users from accessing them.
Operational Threat Intelligence
Operational CTI provides insights into threat actor identities, tools, motivations, ongoing campaigns, and TTPs (tactics, techniques, and procedures). Operational intelligence helps inform threat hunting, training, vulnerability management, and other security functions.
Key Consumers: Malware reverse engineers, forensic investigators, threat hunters leverage adversary intelligence to support incident response and search for indicators of attack aligned to that actor across the environment. For instance, understanding how the Russia-linked APT29 group typically establishes initial access can help focus hunts for related activity.
Strategic Threat Intelligence
Strategic CTI analyzes the risk landscape and your organization‘s exposure in light of business priorities, industry threats, critical assets, potential impact, and vulnerabilities. Strategic intelligence guides executive decision making, budgeting, and overall security strategies.
Key Consumers: CISOs, security leaders, and business executives leverage strategic assessments to make smart, aligned investments in security capabilities that mitigate the most consequential risks. An example is using CTI to inform secure digital transformation initiatives across your organization‘s supply chain based on software vulnerability risks.
The Mounting Impact of AI and Machine Learning on CTI
Artificial intelligence and machine learning are playing an increasingly pivotal role across the cyber threat intelligence lifecycle:
-
Automating Threat Discovery – Natural language processing techniques mine open source (OSINT) and dark web forums to surface emerging threats and monitor adversary chatter. Machine learning models can detect IOC patterns and clusters automatically.
-
Accelerating Alert Triage – By automatically filtering noise and recognizing malicious behaviors based on past learning, AI helps focus the efforts of analysts on the most critical threats within massive alert volumes.
-
Speeding Incident Response – AI techniques like neural networks uncover non-obvious relationships in data and provide insights into threat behaviors by correlating signals from across siloed tools. This significantly reduces investigation time.
-
Strengthening Defenses – By applying AI algorithms to model attacker dwell time, organizations can identify security gaps ripe for exploitation and intelligently strengthen controls.
-
According to cyber threat intelligence firm Recorded Future, their AI engine can process over 1 billion security events per day. This is equivalent to the daily workload of approximately 9,000 threat analysts working 8-hour shifts! The scale and efficiency gains enable organizations to get tremendous value from CTI programs.
Additionally, a 2022 MITRE study found AI-enabled CTI can accurately identify 85% of known threats compared to just 45% detection by humans alone. The combination of AI and human analysis is critical for converting vast threat data into actionable intelligence.
Key Benefits of Cyber Threat Intelligence
Leveraging CTI delivers a range of benefits that tangibly improve your security posture and reduce business risk.
-
Earlier Threat Detection – By ingesting and correlating CTI, you can recognize Indicators of Compromise linked to known bad actors up to 30% faster according to SANS research. This minimizes dwell time.
-
Rapid Incident Response – With detailed adversarial context from CTI, you can cut incident investigation time nearly in half. High-fidelity intelligence answers key questions needed for response quickly.
-
Proactive Risk Mitigation – By knowing the most likely threats facing your organization, you can prioritize vulnerabilities to patch proactively and strengthen defenses before attacks occur.
-
Optimized Security Investments – Strategic intelligence-driven risk assessments enable executives to make cost-effective security investment decisions.
-
Enhanced Security Awareness – Curated threat briefings provide personnel with timely, relevant guidance on evolving social engineering schemes and other tactics to watch for.
-
Improved Compliance – Threat intelligence gives you audit-ready evidence of a proactive, risk-based approach to security assessments and due diligence.
Effective utilization of CTI shifts your organization to a more proactive, threat-centric security model that reduces overall business risk. But realize the maximum benefit, it‘s critical to avoid common pitfalls.
Avoiding Pitfalls for CTI Success
While threat intelligence offers tremendous security and risk reduction value, you need an effective strategy tailored to your organization to maximize results and avoid the following pitfalls:
-
Lack of Analytical Skills – It‘s not enough to merely accumulate threat data. You need skilled analysts to derive strategic insights from CTI tailored to your business and risk environment. Consider investing in developing this specialized expertise, potentially supplemented by outside experts.
-
Poor Integration & Utilization – Ensure intelligence gets operationalized across security workflows and tools like the SIEM. Provide wide accessibility to data across teams from security operations to threat hunting so it gets acted upon.
-
Information Overload – Carefully vet and prioritize CTI feeds to focus on the most relevant threats to your critical assets and attack surface – don‘t drink from the firehose. Avoid flooding teams with threat data that causes alert fatigue.
-
Complacency – View CTI as an enabler of your security program, not a replacement. Threats evolve quickly, so threat intelligence must be ongoing and updated continuously as adversaries shift tactics.
With the right strategy customized to your organization‘s maturity level, threat intelligence provides one of the highest ROIs in security. But it requires thoughtful implementation tailored to your unique needs. Pitfalls stem from treating CTI as one-size-fits all rather than the unique decision advantage it can offer.
Evaluating Leading Vendors for Cyber Threat Intelligence
Many security technology vendors provide cyber threat intelligence capabilities. Here are key factors to evaluate when selecting a solution aligned to your needs:
Breadth of Coverage – Look for CTI sources spanning open source intelligence, dark web, threat feeds, and more to get extensive visibility.
Adversarial Context – Seek actionable insights into threat actor motivations, behaviors, and campaigns – not just IOCs.
Strategic Analysis – Require strategic risk analysis, not just technical data, to inform business context.
Curated Intelligence – Demand expert human analysis to filter noise and ensure relevance to your organization and industry.
Integration & Automation– Prioritize turnkey integration with existing security infrastructure to maximize operational leverage.
Client Base & Reviews – Validate vendor credibility through their experience supporting complex organizations.
Leading CTI vendors to evaluate include:
-
Recorded Future – Powered by natural language processing and machine learning to mine open source, deep/dark web, and aggregate feeds.
-
Anomali – Optimizes threat feeds and integrates with clients‘ security infrastructure to identify threats. Recently acquired Intel 471.
-
LookingGlass Cyber – Offers solutions tailored to sectors like financial services, energy, aerospace, and more.
-
Sixgill – Specializes in CTI via automated dark web intelligence collection and analysis with AI.
-
Flashpoint – Acquired by Proofpoint, provides finished human-analyzed intelligence to defend against cybercrime and targeted threats.
-
ProtectWise – Cloud-native network detection with CTI integrations including automated OSINT collection.
See our guide on selecting a Top Threat Intelligence Platform for more vendor evaluation criteria.
Conclusion and Key Takeaways
With adversaries only growing more sophisticated, leveraging cyber threat intelligence is now crucial for security teams seeking to gain an advantage against evolving threats. The benefits for detection, response, and risk reduction are substantial.
Key takeaways for you as a security leader include:
- Prioritize a threat-centric approach to security strengthened by comprehensive CTI tailored to your organization‘s risks.
- Carefully vet threat intelligence sources, focusing on relevance over sheer volume. Seek out both external and internal data.
- Support CTI analysts as a vital capability – data science skills are hugely beneficial for maximizing this role.
- Ensure integration of intelligence into security workflows and tools to drive action for higher ROI.
- View CTI as an intelligence-driven business enabler, not a tactical tool. Require strategic insights beyond IOCs.
The threats today‘s organizations face are too sophisticated and frequent to rely solely on hindsight. With accurate, actionable cyber threat intelligence, you can work proactively and make smarter security investments driven by risks that matter most. But implementation requires an effective strategy based on your organization‘s maturity, resources and risks.
To learn more about maximizing cyber threat intelligence to strengthen your security posture in 2024, download our comprehensive CTI guide: