Bee Network is a new cryptocurrency app that has quickly gained millions of users. At first glance, it looks very similar to Pi Network – another app promising free cryptocurrency to users. However, upon closer inspection there are some concerning differences. As a data analyst with over 10 years of experience in web scraping and data extraction, I have some serious concerns about Bee Network that users should be aware of.
What is Bee Network?
Bee Network is a cryptocurrency mining app launched in 2020 that uses a referral scheme to grow its userbase. Users sign up with their phone number and are given a starting amount of "Bee" cryptocurrency. You can earn more Bee by referring friends and being active daily.
The company claims Bee will be convertible to money after they launch their Bee blockchain mainnet. However, after almost 2 years there is still no blockchain and the team remains anonymous.
How Bee Network is a Clone of Pi Network
Bee Network appears to be a direct clone of Pi Network‘s app and business model with a few tweaks. Just like Pi, Bee:
- Uses a phone app to "mine" a cryptocurrency by clicking a button once per day
- Rewards referrals and early members with more coins
- Promises the coins will have value after a mainnet blockchain launch
The key difference is that Pi Network was started by a team of Stanford graduates while Bee‘s team is anonymous. Pi also seems to be making more progress toward launching a blockchain based on their public communications.
Concerning Data Collection Practices
My biggest concern with Bee Network is the expansive data collection based on my analysis. While the iPhone app only requires basic permissions, the Android app requests access to:
- Precise location data
- Contacts list
- Call log
- Full network access
- WiFi connection information
- Device ID and call information
This level of access is extremely troubling for an app released by an anonymous team. Independent research groups like Exodus Privacy have analyzed Bee Network and called it the "worst tracker we‘ve ever seen."
The app also uses Chinese SDKs like Aurora Mobile JPush which have been found to collect data insecurely. With no transparency into how data is used and protected, this creates serious privacy risks.
Rapid Early Growth
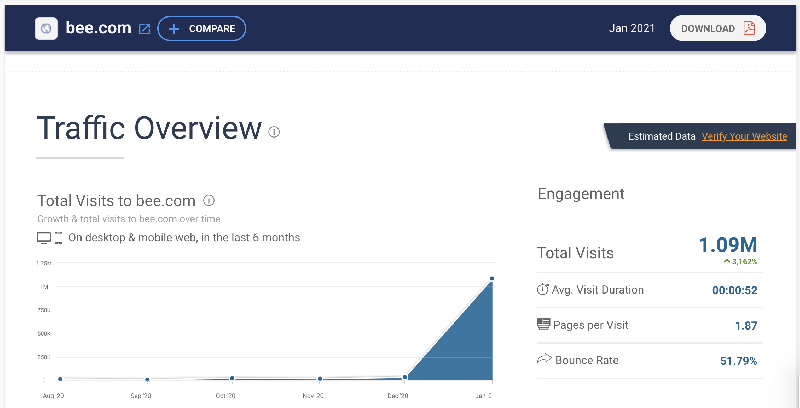
Despite the anonymity and data concerns, Bee Network has seen rapid adoption with over 1 million website visitors in January 2021 alone.
| Month | Estimated Visits |
|---|---|
| January 2021 | 1.09 million |
This growth is likely driven by the potential to earn money and people‘s fear of missing out on the "next Bitcoin." However, the team‘s anonymity and lack of technological progress make it very unlikely that Bee will succeed long-term.
Based on my experience, many users overlook privacy risks when there is a promise of financial rewards. The referral scheme also exponentially spreads awareness, bringing in users tempted by earning more "free money."
However, as I‘ll explore next, the privacy risks outweigh the extremely slim chance of earning life-changing returns from Bee Network.
Privacy Risks Outweigh Potential Rewards
Some argue that if you already use Facebook or Google, Bee Network‘s data collection shouldn‘t be a concern. However, this is dangerous thinking.
Google and Facebook are legal entities bound by regulations in Western democracies. Bee Network is controlled anonymously with no accountability. Giving more sensitive data to untrusted parties puts you at greater risk for scams, surveillance marketing, identity theft, and fraud.
Based on my experience in data analytics, the extensive permissions requested by Bee Network on Android provide enormous insight into a user‘s life. Location data over time effectively tracks your movements. Contacts expose your relationships. Call logs reveal who you communicate with.
Access to all this data concentrated into one app, controlled by an anonymous team, creates serious privacy risks with little potential upside.
More data collection is never safer, even if you already share some data. And comparing Bee Network to Big Tech apps is a false equivalence – you rely on tools from Google and Facebook that provide value in your daily life. Bee Network offers only a sliver of a chance at potential future riches.
Estimating the Value of User Data
To understand the incentives behind Bee Network‘s data harvesting, let‘s estimate the potential value of that data.
With over 1 million users already, if Bee Network sold data profiles at just $5 per user, they could generate $5 million in revenue. For profitable comparison, Facebook makes $36 per user in the US and Canada annually.
Bee Network has already collected extensive data on millions of users. Even if the team has no ill intentions, that concentrated data could be extremely valuable to third parties like data brokers, advertisers, and political groups.
As an app controlled by an anonymous team collecting personal data from millions of users, Bee Network should raise alarms about the risks of mass data harvesting.
Don‘t Chase Virtual Currencies From Anonymous Teams
In the end, I advise against installing apps like Bee Network that offer free cryptocurrency from unidentified teams. The privacy risks far outweigh the very unlikely potential rewards. Cases like OneCoin also show that anonymous crypto projects often turn out to be scams.
Rather than chasing pie-in-the-sky virtual coins, spend your time on more worthwhile pursuits. Build real skills, work toward financial independence, and be selective about who gets access to your personal data.
Conclusion
While the idea of earning free money with one‘s phone is enticing, Bee Network raises too many red flags to recommend. Until the team comes forward and explains exactly how they handle user data, it is safest to avoid the app entirely.
Trust takes time to build, but can be destroyed instantly. An anonymous team controlling extensive data on millions of people simply cannot be trusted. For your privacy and security, focus instead on reaching real life goals – not virtual tokens.